Introduction
The Evolution of Blockchain
Related Works
Blockchain for Secure Health Information Exchange
Patient-Centric Electronic Health Records (EHRs)
Enhancing Clinical Trials and Drug Supply Chain Management
Streamlining Clinical Data Management
Existing Challenges
Primary Components of the System
P2P Networks
Proof of Work (PoW)
Blockheader Format
Chord-Based Distributed System
Overlay Network
Patient-Centric Electronic Health Records (EHRs)
System Model and Architecture
P2P Network Nodes
Blockchain Ledger
Smart Contracts
Distributed Hash Table (DHT)
Client Interface
Communication Protocols
Load Balancing and Scalability
Security and Privacy Measures
Network Architecture
System Model and Architecture
System Model Analysis
Security Analysis
Digital Signatures and Cryptographic Security
Conclusions
Future Works
Introduction
Personal Health Information (PHI) encompasses all activities that connect patients with healthcare providers, facilitating the organization, management, and accessibility of sensitive health information. The decentralized system is built on the principle of enhancing healthcare services [1] by efficiently organizing and directing PHI. However, challenges in data management persist, necessitating a proactive strategy from developers to address these issues. In recent years, healthcare organizations have increasingly relied on cloud storage and centralized databases [2] to provide real-time updates on patients. This medical information includes essential data such as gender, date of birth, and care plans. However, the fragmented nature of PHI, maintained across multiple healthcare providers, often results in isolated patient records. Typically, this data is stored within provider-specific databases, limiting patients' access and control over their own records. Consequently, healthcare providers may transmit PHI in various formats, creating barriers to efficient data sharing and access for both patients and providers. To address these challenges, it is essential to develop a robust decentralized system for managing PHI.
This paper proposes a novel architecture for managing PHI using blockchain technology. In this model, data is disseminated via a peer-to-peer (P2P) [3] overlay network, with verified transactions securely stored on the blockchain. To ensure the integrity of each transaction, miners must complete a proof-of-work (PoW) puzzle before adding a new block to the blockchain. This structure not only enhances data security but also enables stakeholders to trace the entire history of PHI, as each transaction is recorded within the chain. Moreover, by segmenting PHI into distinct blocks, our model allows for easier access and management for various healthcare entities.
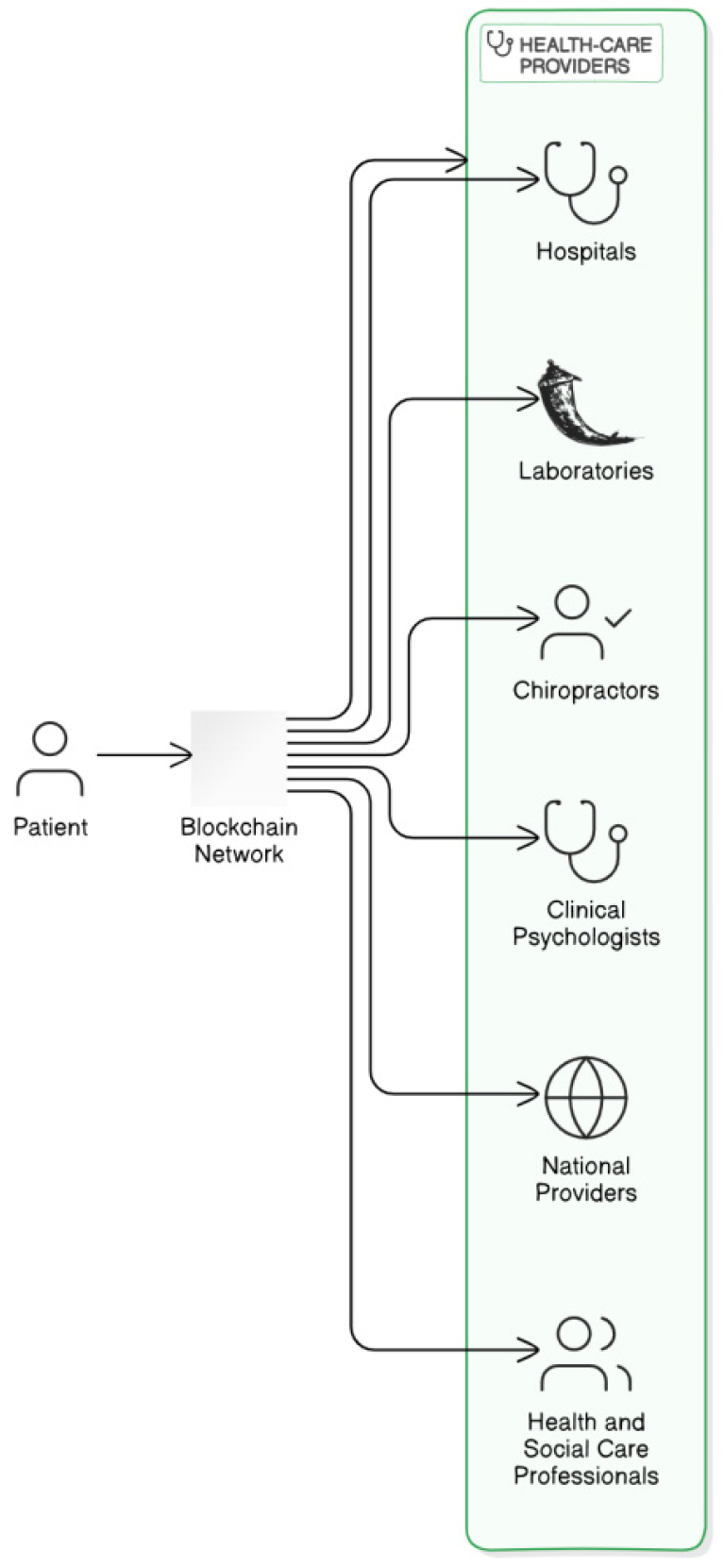
PHI originates from a wide range of healthcare providers, including physicians, chiropractors, medical psychologists, national health services, and laboratories [4, 5]. This proposed model facilitates seamless interoperability and traceability across the healthcare ecosystem by ensuring that PHI is securely managed and accessible within a decentralized, blockchain-based framework.
The Evolution of Blockchain
Blockchain generation has swiftly developed given that its inception with Bitcoin in 2008 as a decentralized forex [6]. This innovation has paved the manner for numerous packages throughout numerous industries. The creation of smart contracts on platforms like Ethereum in 2015 allowed for the improvement of decentralized applications (dApps), transforming how transactions and agreements are executed. Industries which include deliver chain control, finance, healthcare, and real estate have harnessed blockchain's abilities to enhance transparency, security, and efficiency [7]. Companies like IBM and Walmart use blockchain for traceability in deliver chains, at the same time as economic offerings are revolutionizing go-border payments and creating decentralized finance (DeFi) structures that reduce reliance on intermediaries.
Blockchain era serves as a foundational records structure for growing decentralized ledgers, prepared in a serialized layout [8]. Each block inside a blockchain carries a collection of transactions, a hash of the previous block, a timestamp, a block praise, and a completely unique block quantity, amongst different factors. This decentralized nature guarantees that every node within the blockchain community continues a same reproduction of the facts, fostering consistency and transparency. Blockchain now not best stores statistics but also establishes protocols for updating that information [9]. Its key advantages lie in automating approaches and creating transparent, secure programs. By mitigating the risks of fraud and corruption, blockchain addresses numerous challenges confronted in conventional structures. This era paves the manner for a brand-new era of transactional applications and streamlined commercial enterprise approaches, cultivating believe, responsibility, and transparency—crucial pillars of contemporary commerce [10]. In contemporary trade and industry, agree with is underpinned by using cryptographic protocols integrated in the machine, ensuring transaction integrity. Traditional community architectures, including centralized networks, perform by way of routing facts via a crucial node before achieving the intended recipient. This version inherently is based on intermediaries, introducing capacity vulnerabilities [11]. In comparison, decentralized models distribute statistics across the community without intermediaries, getting rid of reliance on a single server and mitigating the danger of single factors of failure. This decentralized method complements resilience and efficiency. Blockchain technology finds programs throughout various sectors, inclusive of financial registries, operational facts, and contractual agreements.
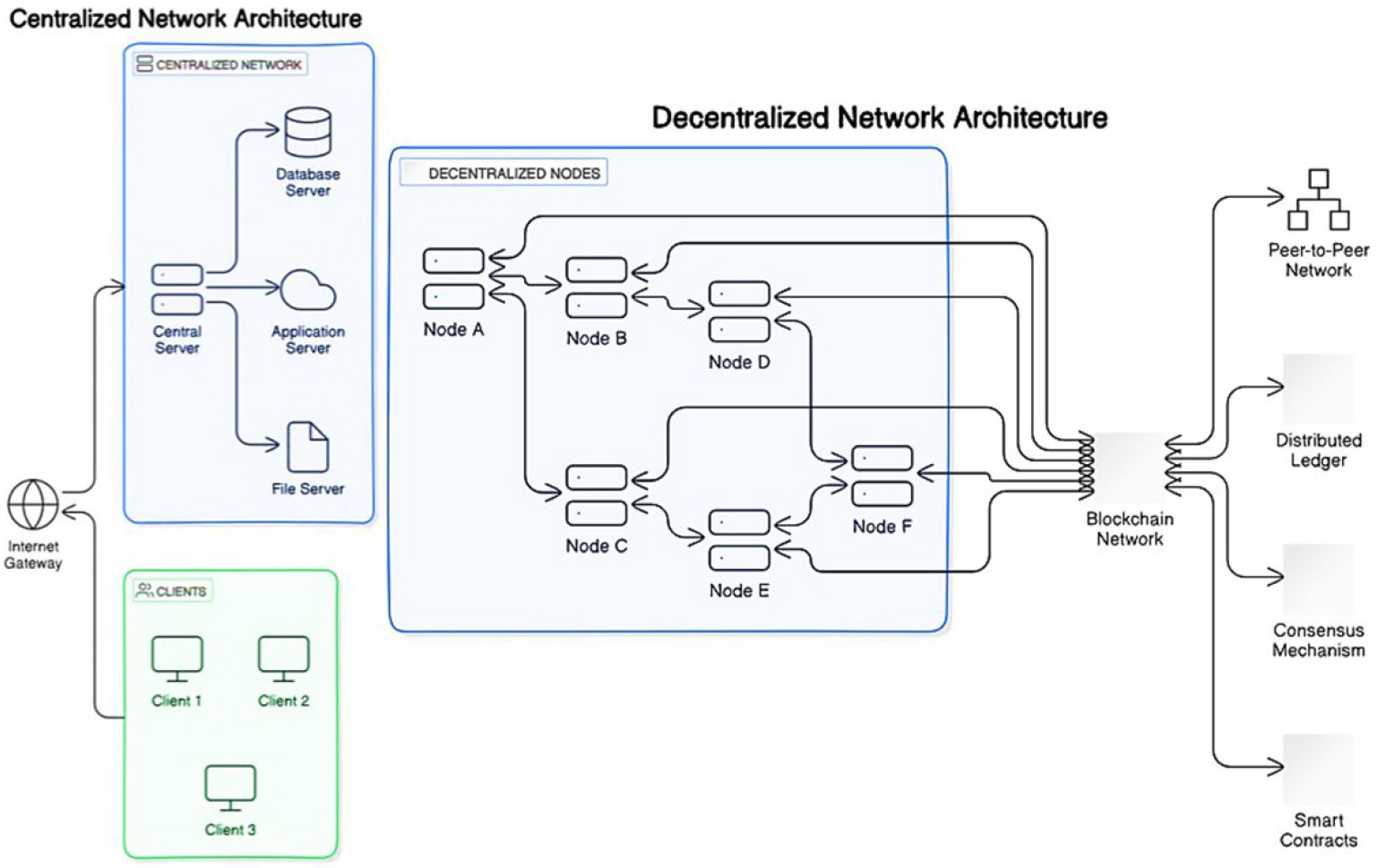
The “Centralized and Decentralized Network Architecture” illustrated in Figure 1 contrasts two fundamental networking paradigms, every with its own characteristics, blessings, and challenges. In a centralized community, all essential components, which includes the crucial server, database server, application server, file server, and customers, converge on a single hub [12]. This architecture simplifies control and enhances protection, as all resources are stored in a single place. However, it introduces a single point of failure; if the vital server is going down, the complete network will become inoperable. In assessment, the decentralized network structure distributes additives and sources throughout more than one impartial node, bearing in mind direct peer-to-peer conversation.
This structure enhances scalability, reliability, and security by using getting rid of the reliance on a government, thereby lowering the risk of a single factor of failure. Each node can anticipate various roles, participate in allotted selection-making, and leverage blockchain technology for stable facts management through a shared distributed ledger and consensus mechanisms [13]. While decentralized structures offer blessings in terms of resilience and transparency, they can also present complexities in management and ability performance challenges because of the consensus procedures concerned. Understanding these architectural differences is crucial for studying superior P2P conversation structures, mainly in packages like clinical data sharing the use of blockchain generation.
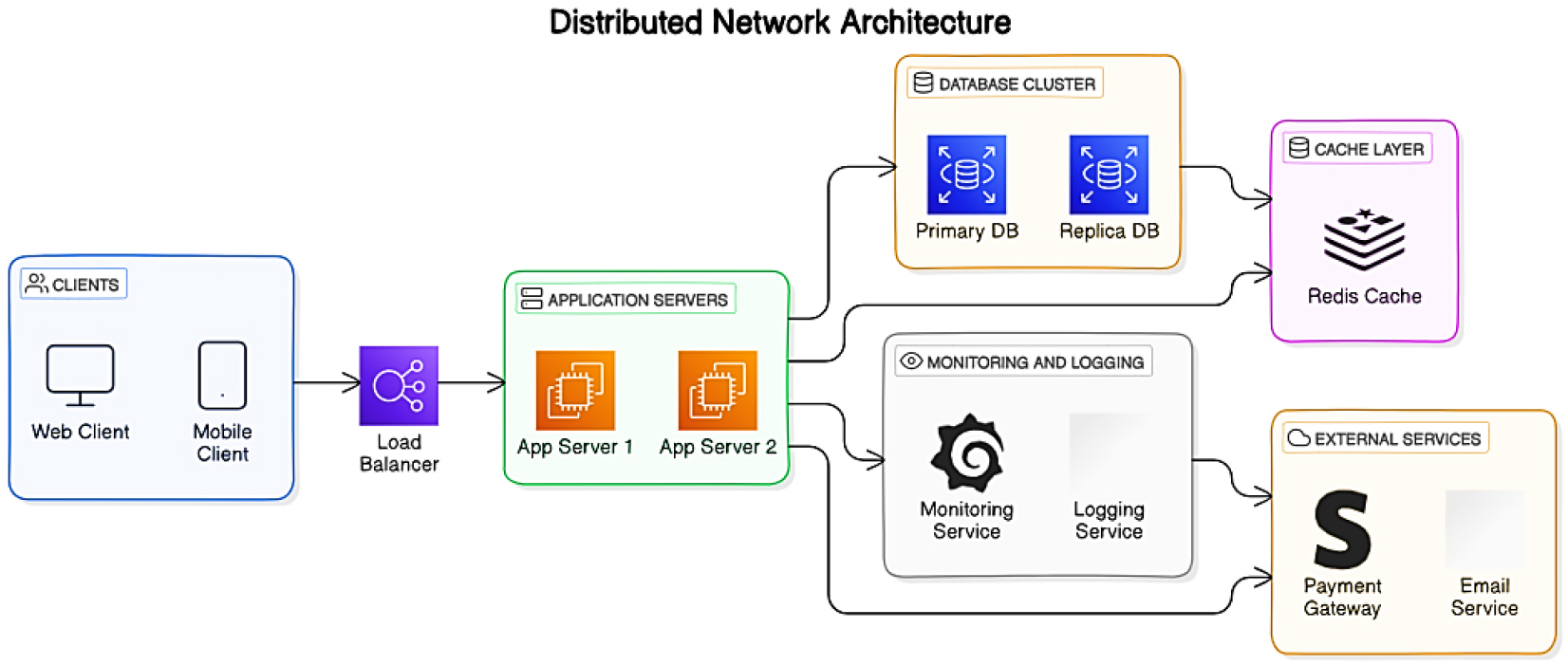
The “Distributed Network Architecture” illustrated in Figure 2 provides a complicated setup wherein components and sources are spread throughout more than one servers, substantially improving scalability, reliability, and overall performance in comparison to centralized systems [14]. This architecture comprises numerous key components: customers, which can be numerous devices getting access to the community; a load balancer that distributes incoming traffic throughout multiple application servers to improve overall performance and fault tolerance; application servers that manage purchaser requests; a database cluster together with a number one and copy databases for records redundancy; a cache layer for immediate statistics retrieval; and tracking and logging systems to track community health and troubleshoot troubles. In this architecture, a patron sends a request to the burden balancer, which then directs the request to an to be had application server for processing.
The benefits of this dispensed architecture consist of stronger scalability, reliability, progressed overall performance thru load balancing and caching, and fault tolerance [15, 16], permitting the gadget to manage character factor failures without affecting typical capability. However, it introduces complexity in control and necessitates robust security measures for each issue. While this structure does now not at once depict a P2P community, its standards are incredibly applicable to blockchain-based totally P2P structures, which inherently distribute nodes across diverse places to make certain resilience and security. Key takeaways for your research include an expertise of dispensed systems, the software of blockchain generation in growing secure decentralized networks, and the performance implications of distributed architectures, particularly within the context of scientific information sharing.
As blockchain keeps to mature, its ability programs are increasing similarly. In healthcare, it enhances affected person information control, making sure integrity and security [17, 18]. Voting structures leverage blockchain for transparent elections, and digital identity verification projects empower people to manipulate their identities securely. The strength zone is likewise exploring peer-to-peer electricity trading fashions, while actual property is streamlining assets transactions through smart contracts. Overall, the evolution of blockchain indicates a transformative shift throughout industries, fostering increased efficiency, transparency, and protection in diverse operational frameworks.
Related Works
The integration of blockchain generation into healthcare systems has emerged as a ground-breaking solution to many continual challenges [19], mainly in terms of records security, interoperability, patient privacy, and operational performance. As the demand for decentralized structures grows, several studies have highlighted the advantages and capability applications of blockchain within the healthcare quarter, mainly in facilitating peer-to-peer (P2P) conversation for clinical facts [20].
Blockchain for Secure Health Information Exchange
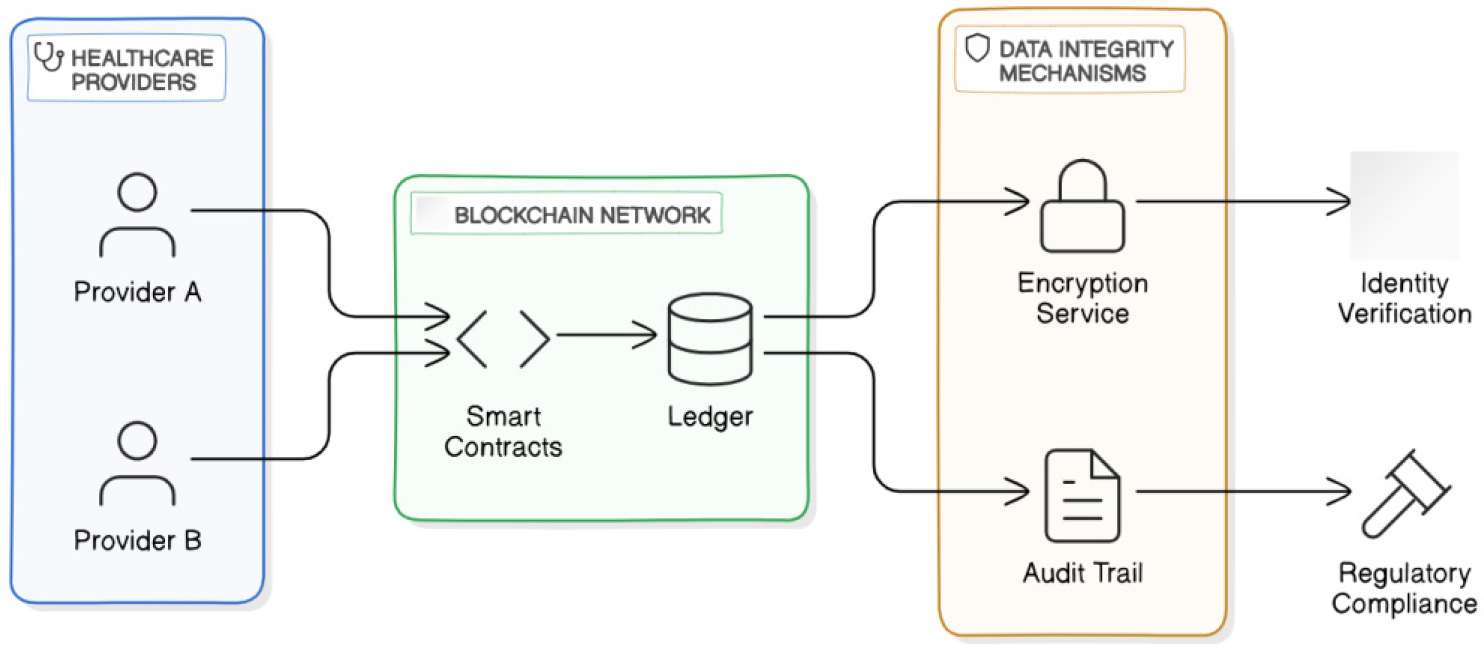
An extremely good observe via Zhang et al. (2019) investigates the benefits of employing blockchain for secure health facts change [21, 22]. The authors propose a blockchain-based totally framework designed to ensure information integrity, confidentiality, and actual-time get right of entry to scientific facts among various healthcare vendors. Their studies emphasize the want for a decentralized method, which mitigates risks related to records breaches and unauthorized access, hence fostering trust amongst stakeholders inside the healthcare environment. This has a look at illustrates how blockchain can create a secure channel for health statistics sharing, improving patient care and collaboration among companies. Further, Figure 3 shows the glimpse of secure health Blockchain framework.
Patient-Centric Electronic Health Records (EHRs)
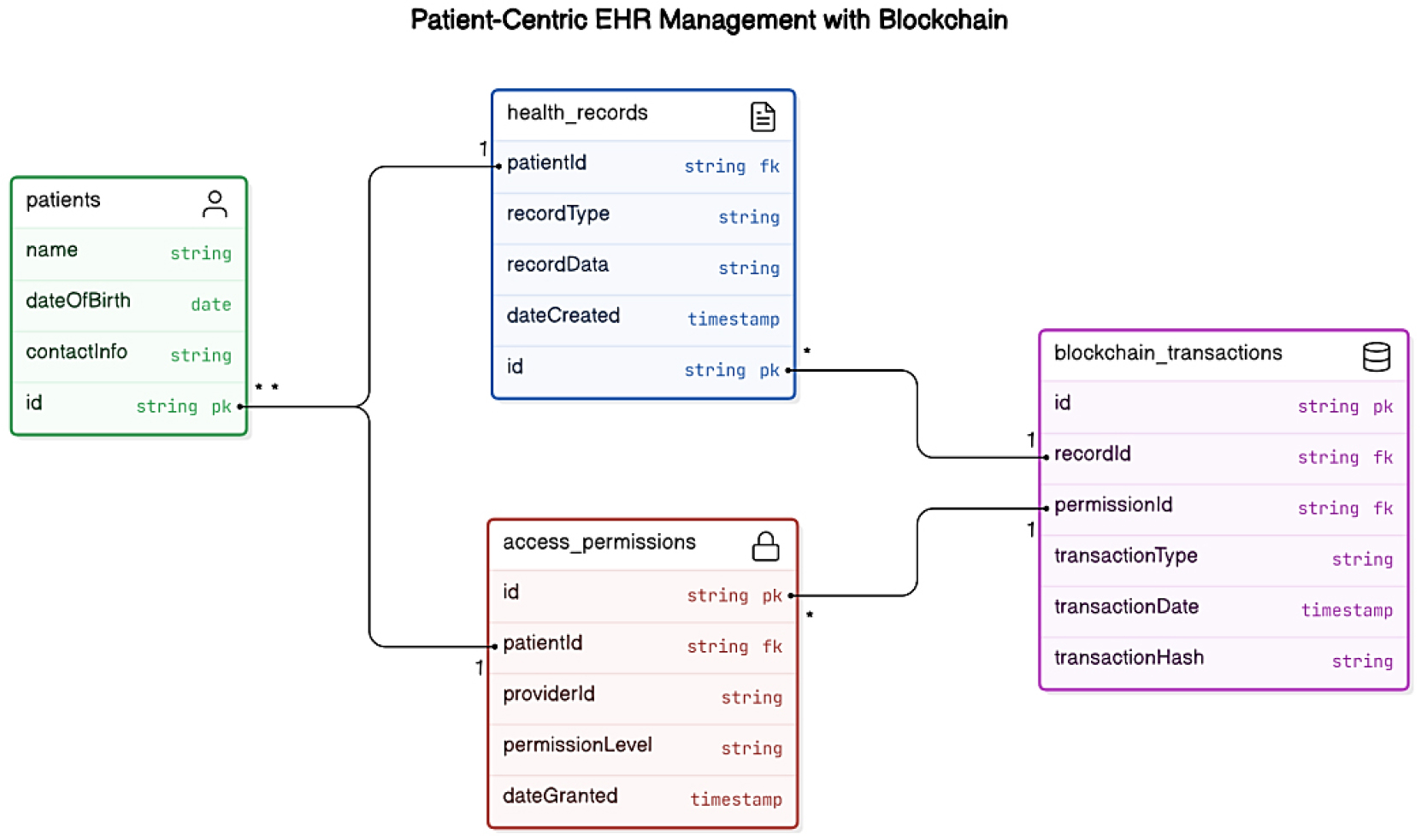
In a related take a look at, Kuo et al. (2017) explores the results of blockchain technology for electronic health statistics (EHRs) [23, 24]. They introduce a conceptual version that illustrates how blockchain can improve interoperability across diverse healthcare structures while empowering patients with greater manage over their fitness data. By enabling patients to dictate who accesses their data, the proposed framework aligns with modern trends in patient-centred care [25, 26], in which patient autonomy and involvement are paramount. This study highlights the importance of decentralized architectures, which mitigate problems related to traditional centralized databases, such as vulnerabilities to records breaches and mismanagement, in addition advocating for the integration of blockchain as a way to beautify affected person engagement and protection, as shown in Figure 4.
Enhancing Clinical Trials and Drug Supply Chain Management
Additionally, Mettler (2016) gives a comprehensive overview of blockchain programs in healthcare, categorizing them into various domains including clinical trials, drug deliver chain management, and P2P health data sharing. The writer elucidates how blockchain can decorate the performance of scientific trials by means of enhancing records provenance and transparency, thereby reducing fraud and errors. Mettler’s research highlights the role of clever contracts in automating processes and making sure compliance with regulatory standards, which could in the long run cause greater operational efficiency in healthcare. The usage of blockchain in scientific trials can assist create immutable facts of affected person consent, trial protocols, and results, thereby fostering duty and agree with inside the research procedure.
Streamlining Clinical Data Management
Research conducted by Angraal et al. (2017) in addition investigates the effect of blockchain on medical records control [27, 28]. They propose that blockchain can streamline statistics procedures while maintaining a high degree of safety and integrity. The take a look at emphasizes the need for developing strong frameworks that comprise P2P conversation protocols to facilitate the seamless exchange of clinical statistics amongst healthcare stakeholders [29, 30]. They argue that real-time records get right of entry to for healthcare carriers is vital for making knowledgeable decisions which could in the long run improve affected person consequences. Their findings imply that imposing blockchain-based systems can reduce administrative burdens and beautify the accuracy of clinical data.
Furthermore, a scientific overview by way of Davis et al. (2021) evaluates the cutting-edge state of blockchain implementation in healthcare settings [31, 32]. The authors categorize the blessings and limitations of blockchain era, identifying key areas for in addition exploration, inclusive of scalability, regulatory compliance, and person reputation. Their findings monitor that at the same time as blockchain offers tremendous benefits in phrases of protection and transparency, demanding situations stay in attaining consumer-pleasant interfaces and ensuring compliance with healthcare policies. They call for multidisciplinary research efforts to bridge these gaps and force the successful adoption of blockchain in medical packages. This comprehensive evaluation underscores the importance of knowledge each the technological and human elements that affect the deployment of blockchain solutions in healthcare environments.
In the context of the growing telemedicine fashion, Saha et al. (2022) looks into the position of blockchain in permitting stable telemedicine offerings. Their studies highlight the need for stable statistics sharing between sufferers and healthcare carriers in far off consultations. The authors endorse a blockchain-based totally answer that incorporates P2P conversation to beautify the privacy and safety of telemedicine interactions. This study underscores the relevance of blockchain in present day healthcare delivery fashions, especially in mild of the COVID-19 pandemic, which has elevated the adoption of telehealth offerings. Their findings advise that imposing blockchain can build affected person agree with in telemedicine structures by way of ensuring the confidentiality of sensitive fitness facts.
Another issue explored inside the literature is the impact of blockchain on medical deliver chains. Kumar et al. (2021) talk how blockchain may be used to enhance the traceability and authenticity of scientific merchandise [33, 34], thereby preventing counterfeit drugs and making sure patient protection. Their studies highlight the position of P2P communication in facilitating real-time monitoring of products all through the supply chain [35]. The authors suggest a blockchain-primarily based answer that integrates Internet of Things (IoT) devices for tracking environmental situations during transportation and storage, ensuring that merchandise keep their efficacy. This looks at illustrates the wider implications of blockchain in improving the general protection and reliability of healthcare supply chains.
Overall, the prevailing frame of literature underscores the transformative capability of blockchain generation in enhancing P2P communique within healthcare. While great development has been made in demonstrating the viability of blockchain applications [36], further research is vital to cope with implementation challenges, scalability issues, and the combination of blockchain with current healthcare infrastructures. Future research needs to consciousness on actual-world case implementations, the improvement of nice practices, and the exploration of hybrid models that integrate blockchain with different emerging technology, which include artificial intelligence and the Internet of Things (IoT), to similarly beautify the safety and efficiency of medical records sharing.
Existing Challenges
The implementation of blockchain technology in healthcare faces numerous considerable challenges, in general centered round facts privacy, interoperability, and scalability. First, at the same time as blockchain complements safety and information integrity [37, 38, 39], its decentralized nature can disclose touchy medical information to unauthorized get entry to if right encryption and access manipulate measures aren't in region, raising worries approximately compliance with rules including HIPAA and GDPR. Additionally, the lack of standardized protocols for blockchain implementation leads to interoperability issues, resulting in fragmented systems that avert effective information sharing across special healthcare providers, thereby increasing operational inefficiencies. Furthermore, scalability stays a essential challenge, as many blockchain networks war with performance bottlenecks when dealing with a growing quantity of users and transactions, that can postpone get right of entry to to important affected person information and in the end effect the exceptional of care. Addressing these challenges is vital for a success integration of blockchain in healthcare, necessitating ongoing research and improvement to create strong frameworks that prioritize records privateness, beautify interoperability, and enhance scalability whilst maintaining the inherent advantages of blockchain era.
Primary Components of the System
The proposed device for reinforcing peer-to-peer (P2P) verbal exchange in the healthcare domain is anchored in several essential components, every contributing to the overall performance, safety, and reliability of the network. These components include P2P networks, Proof of Work (PoW), chord-primarily based distributed systems, and overlay networks [40].
P2P Networks
P2P networks function the backbone of decentralized communique, allowing direct interactions among customers without the need for a valuable server, as shown in Figure 5.
In healthcare, this permits for secure and efficient information alternate amongst various stakeholders, including patients, healthcare providers, and research institutions. The community topology may be described mathematically by means of considering the range of nodes (N) and the connections (C):
This equation signifies that each node can potentially connect with every other node, thus enhancing redundancy and fault tolerance within the network.
Proof of Work (PoW)
Proof of Work is a consensus mechanism employed to validate transactions and secure the blockchain against malicious attacks. In a PoW system, miners compete to solve a mathematical puzzle [41], which can be represented as follows:
Where:
• is the hash value of the block.
• is a cryptographic function applied to the block data.
• is a nonce, a variable added to ensure that the hash meets a specific difficulty level.
The trouble is dynamically adjusted based at the average time taken to mine blocks, ensuring that new blocks are brought at a regular charge. This mechanism now not handiest secures the blockchain however additionally incentivizes participants to make contributions their computational assets.
The block header format provided in Table 1 consists of the records for one block which include the model of the block, hash of the preceding block, Merkle root hash, modern issue fee, and the nonce (the quantity of tries to locate the target price). PoW is described as the race between the miners, and the fastest miner who solves the puzzle is the winner and gets a few cryptocurrencies as reward. The more the computational energy of the miner, the more chances to solve the puzzle.
Table 1.
Block Header Format
Blockheader Format
The blockheader layout includes essential elements inclusive of the preceding block’s hash, timestamp, nonce, Merkle root, and transaction remember. The integrity of the blockchain is maintained through linking each block to its predecessor thru cryptographic hashes. This guarantees that any tampering with a block could require recalculating the hashes of all subsequent blocks, that is computationally infeasible.
Chord-Based Distributed System
The chord-based totally disbursed device is a good way to discover and save data in a allotted network. In this gadget, every node is assigned an identifier in a circular space, and statistics is placed based on its hash cost. The set of rules for locating a node can be expressed as:
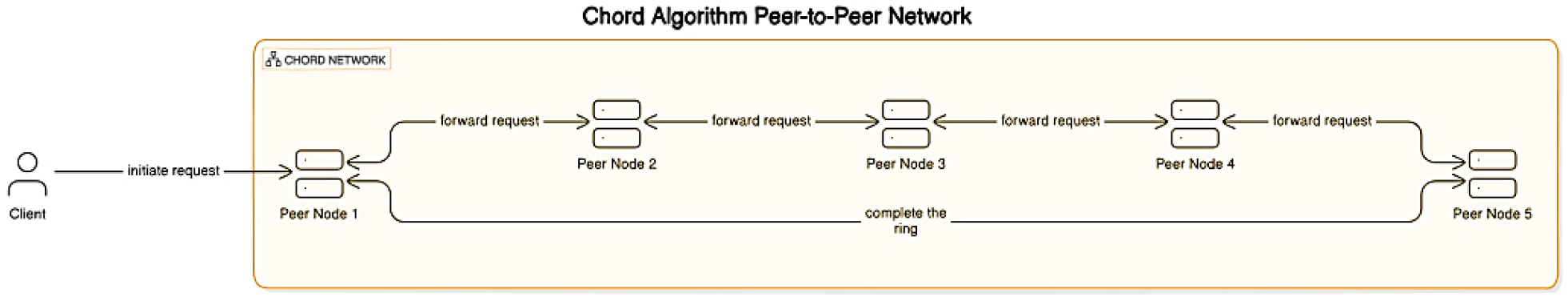
Where (id) is the identifier of the facts to be retrieved. This technique permits for logarithmic time complexity in finding nodes, making it scalable and efficient [42]. The chord set of rules illustrates this node association and the message-passing system involved in finding successors.
Figure 6 illustrates the essential shape of the Chord set of rules, showcasing the interplay between clients and servers. On the customer side, key additives include the document system, block keep, and the Chord protocol itself [43]. Conversely, the server facet incorporates a block shop and the Chord protocol, which enables connections to other servers. A primary function of the Chord protocol is to allow customers to question for a successor (k), accomplishing a question time complexity of O(N), where N represents the wide variety of machines inside the ring topology.
Additionally, the Chord protocol [44] makes use of a distributed hash desk (DHT), a similar information structure designed to perform within a distributed system as opposed to a unmarried process. In this context, the items being controlled are documents identified via particular keys. Load balancing is another crucial issue of DHTs, ensuring that every host stores a more or less identical number of objects. This stability is critical to prevent certain hosts from turning into overloaded with statistics while others continue to be underutilized.
Overlay Network
Overlay networks operate atop existing physical infrastructures, creating virtual pathways for enhanced communication [45]. An overlay network designed for optimal connections among devices in a local area network (LAN) can be modelled using graph theory, where nodes represent devices and edges represent connections. The connectivity graph (G) can be represented as:
Where:
• is the set of vertices (nodes).
• is the set of edges (connections).
This model allows for analysing the network's resilience and optimizing data flow.
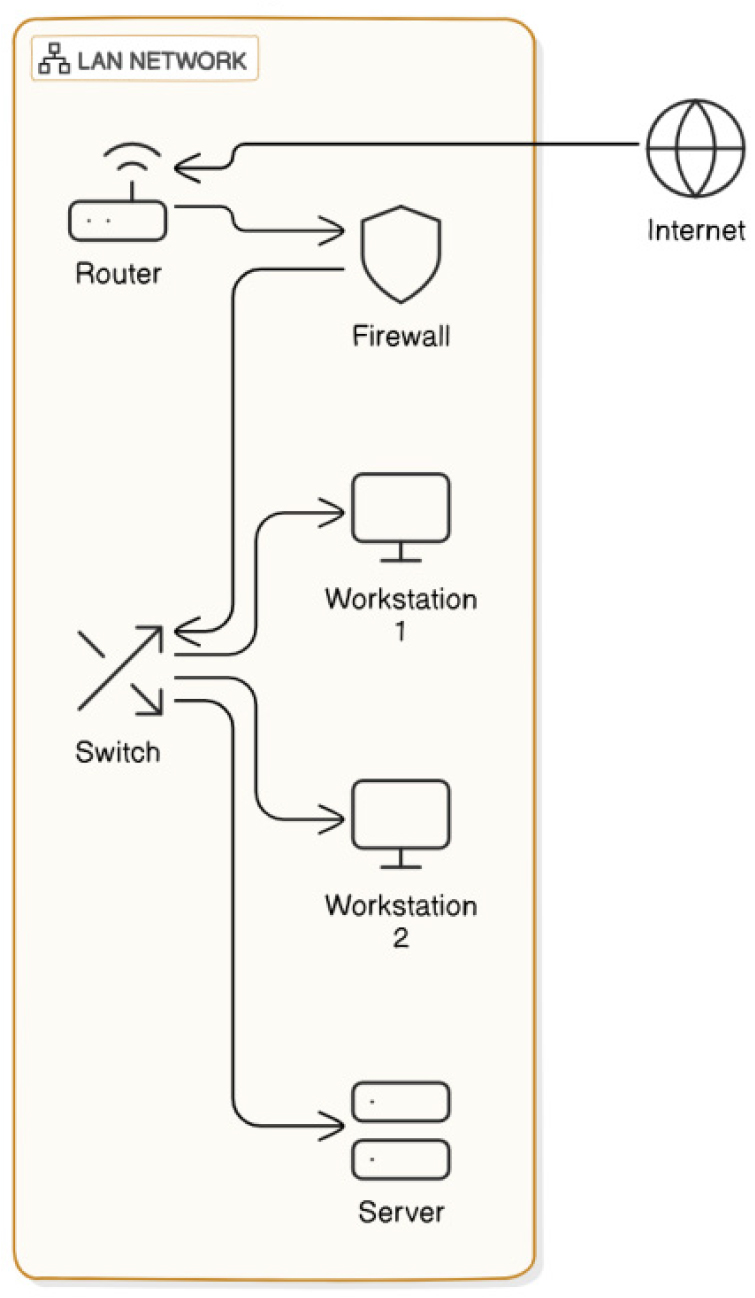
Figure 7 depicts a virtual network illustrating the connections between two local location networks (LANs). An example of an overlay network is a Content Delivery Network (CDN) [46]. A CDN optimizes the transport of static content material from web sites—together with photographs and motion pictures—by using storing copies of this content material in strategically dispensed places throughout the network. When a regular vacationer accesses a website that utilizes a CDN, their request is directed to the closest CDN server, in place of going immediately to the authentic net host. This manner significantly reduces latency and enhances the overall user revel in by using ensuring quicker load instances and advanced accessibility to content [47].
Patient-Centric Electronic Health Records (EHRs)
Understanding the physical paths of connections within the overlay network is crucial for evaluating performance and reliability. The physical path can be defined using:
Where each (n_i) is a node in the physical network. This equation emphasizes the importance of both overlay and physical layers in facilitating seamless communication.
Together, those additives create a robust framework that correctly addresses the demanding situations of medical information sharing in decentralized surroundings. By leveraging P2P networks, PoW, chord-primarily based structures, and overlay networks, the proposed machine targets to enhance the security, performance, and reliability of healthcare verbal exchange, ultimately contributing to improved patient outcomes and more effective healthcare delivery.
System Model and Architecture
The structure of the proposed system is meticulously designed to leverage decentralized standards, facilitating peer-to-peer (P2P) communique for clinical facts sharing. This structure addresses the inherent demanding situations in conventional healthcare records management systems at the same time as improving protection, integrity, and accessibility of touchy medical data. It comprises multiple interrelated additives that feature synergistically to provide a robust framework for records sharing amongst stakeholders within the healthcare ecosystem. The architecture may be visualized as a multi-layered shape such as numerous key additives:
P2P Network Nodes
In this structure, each player in the network—such as healthcare providers, patients, researchers, and regulatory bodies—operates as an impartial node. These nodes can count on various roles, together with statistics companies, requestors, or validators, contributing to the overall functionality of the system. Nodes interact immediately via established P2P protocols, taking into account seamless information exchanges without the want for a primary server. This direct interaction fosters collaborative surroundings, enabling real-time communication and speedy dissemination of information.
Blockchain Ledger
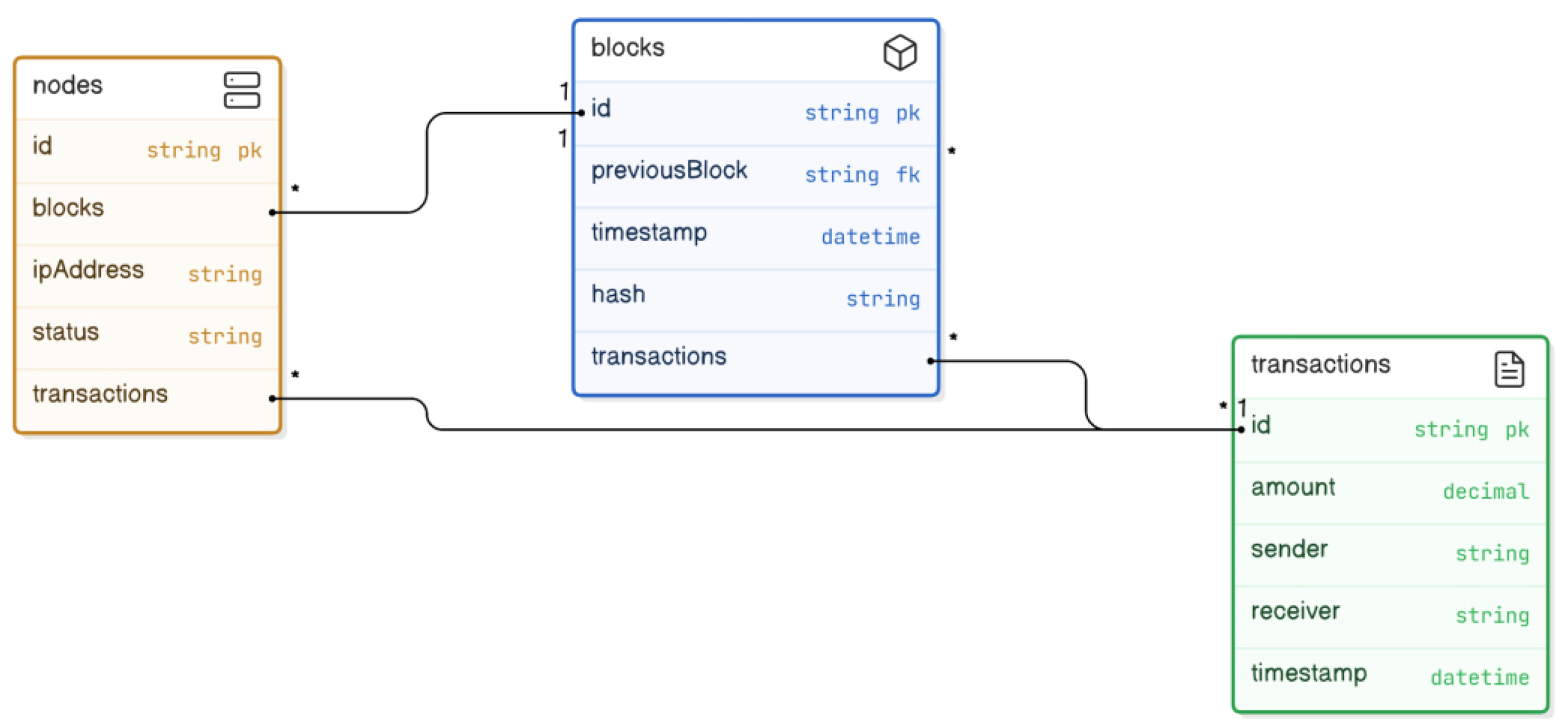
The blockchain ledger serves because the middle of the architecture, providing an immutable and obvious record of all transactions [48]. Each block within the chain carries a unique hash, a timestamp, and a connection with the preceding block, thereby ensuring information integrity. The community employs a consensus mechanism—consisting of Proof of Work (PoW) or Proof of Stake (PoS)—to validate transactions earlier than they're added to the blockchain. This mechanism ensures that all participants agree at the country of the ledger and protects against malicious assaults and records tampering. Medical statistics are saved as transactions within the blockchain, making sure they're secure, verifiable, and retrievable by means of legal events.
This Figure 8 depicts the structure of the blockchain ledger, illustrating how blocks are linked and the components included in each block.
Smart Contracts
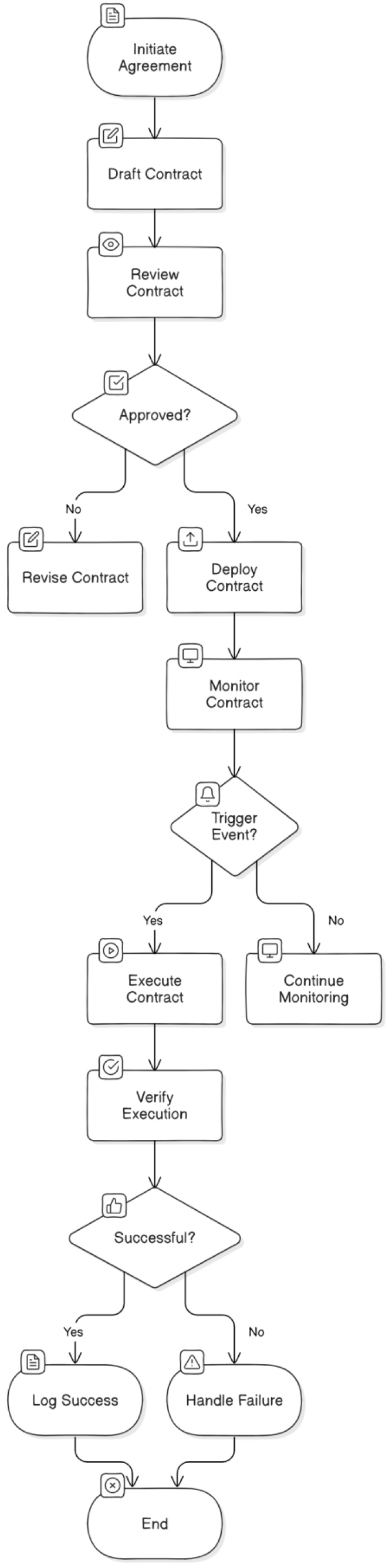
Smart contracts are self-executing digital agreements that encode phrases and conditions without delay into code [49], permitting automated execution of agreements without the need for intermediaries, as shown in Figure 9. In the context of healthcare, smart contracts streamline techniques inclusive of affected person consent control and manipulate over information access permissions, providing a steady and green way to deal with sensitive private health statistics (PHI). This automation reduces administrative overhead, minimizes human mistakes, and guarantees that handiest legal events can get admission to patient facts, thereby improving records security and affected person privateness.
One of the vital benefits of clever contracts is their capability to construct agree with amongst stakeholders. By removing the need for third-birthday party intermediaries, smart contracts reduce the hazard of disputes over records get admission to and consent. Their transparent, self-executing nature permits stakeholders to trace every interplay with the PHI and validate compliance with pre-established terms, decreasing the danger of unauthorized get right of entry to or facts breaches. This transparency also fosters duty, as all parties have visibility into who accessed what facts and under which situations, aligning with regulatory requirements which include HIPAA.
Moreover, clever contracts provide an auditable and stable mechanism for ensuring that each one involved party adhere to regulatory and compliance standards. By embedding regulatory rules and policies inside the settlement code, smart contracts automatically put in force compliance, decreasing the burden on healthcare providers to manually oversee these necessities. This functionality ensures that information coping with processes meet the necessary felony standards, paving the manner for broader adoption of blockchain-based answers in healthcare statistics management. Overall, smart contracts enhance system efficiency, foster trust, and enable a more resilient and compliant healthcare ecosystem.
Additionally, clever contracts provide scalability benefits, making it possible to manage growing volumes of healthcare data as structures develop. In big- scale implementations, together with national healthcare systems or huge health facility networks, the automation provided by means of clever contracts can streamline complex processes concerning more than one stakeholder, including insurance claims, billing, and real-time information sharing between healthcare companies. By automating those multifaceted techniques, smart contracts no longer best improve reaction times however also lessen administrative charges associated with manual data coping with. This scalability and performance make clever contracts a powerful tool for future healthcare models, especially as patient facts volumes and complexity maintain to upward push.
Distributed Hash Table (DHT)
The DHT complements statistics retrieval performance across the distributed community. It maps unique identifiers of medical data to the corresponding nodes, making an allowance for fast get right of entry to and retrieval of facts [50]. As the number of nodes in the network grows, the DHT ensures that the machine can scale efficiently with the aid of preserving a balanced distribution of records and minimizing the weight on person nodes.
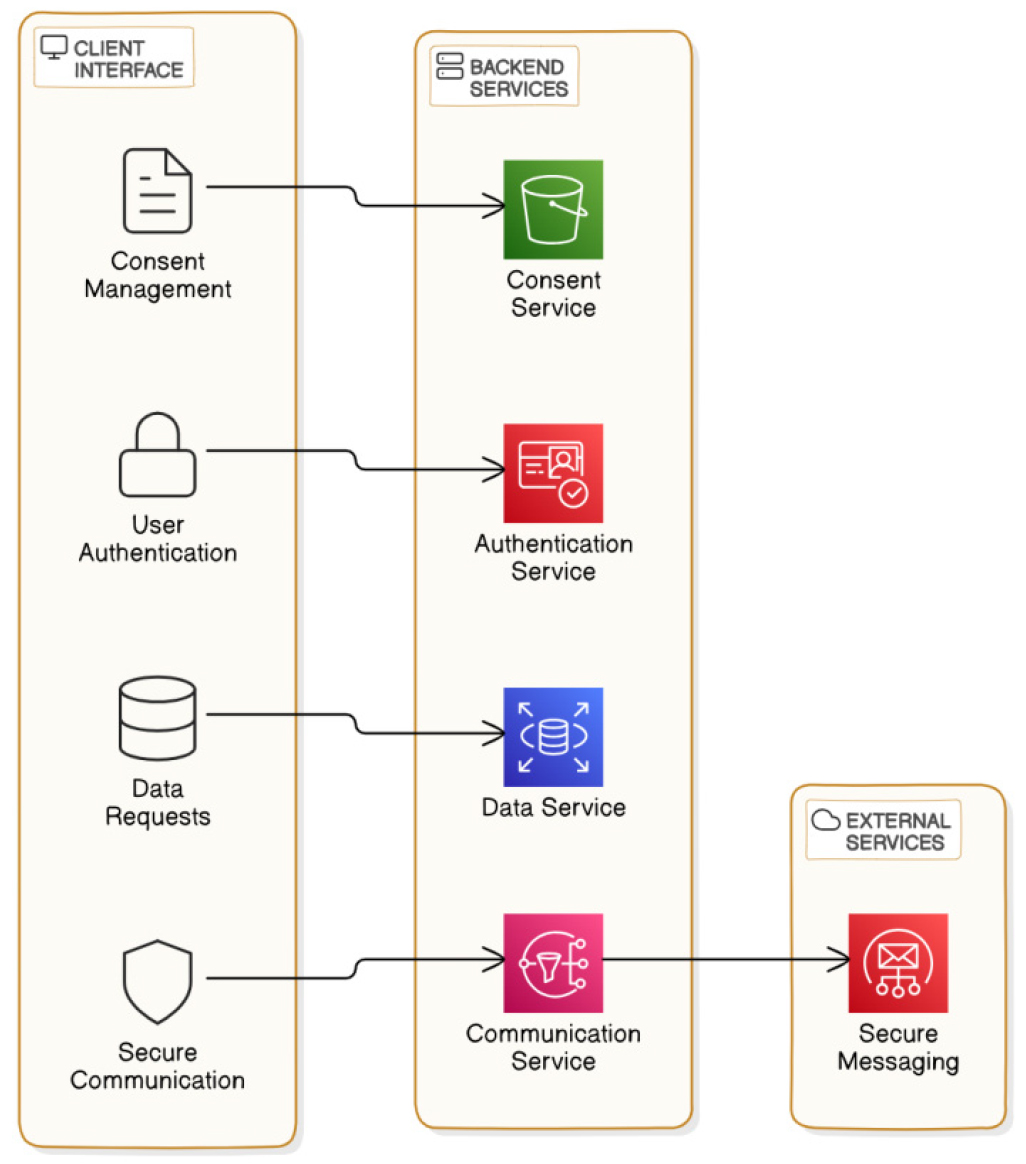
Client Interface
The consumer interface is designed to provide an intuitive and consumer-friendly revel in for diverse stakeholders. It helps multiple devices, along with cellular phones and laptop programs, permitting customers to get entry to the system from anywhere. Through the patron interface, users can post requests for scientific information, control consent settings, and have interaction in stable communications with other nodes. This interface is important for making sure that stakeholders can interact with the gadget efficaciously.
This figure showcases the design of the client interface, highlighting its features and functionality for users, as presented in Figure 10.
The patient and healthcare provider are interconnected within the blockchain network. Healthcare vendors encompass a numerous variety of entities, inclusive of hospitals, laboratories, chiropractors, clinical psychologists, national healthcare agencies, and diverse fitness and social care professionals.
Communication Protocols
The verbal exchange protocols within the structure are crafted to make sure secure, reliable, and efficient data trade. Key elements include:
•Encryption Techniques : All records exchanged between nodes is encrypted using superior cryptographic techniques to preserve confidentiality and prevent unauthorized get entry to. Techniques which includes asymmetric encryption make sure that handiest intended recipients can decrypt the data.
•Integrity Verification : Consensus protocols, coupled with cryptographic hashing, guarantee the integrity of facts during the network. Each transaction ought to be verified via multiple nodes earlier than it is able to be recorded on the blockchain, ensuring that most effective legitimate records is shared.
Load Balancing and Scalability
To enhance performance and useful resource utilization, the system incorporates load-balancing strategies:
•Dynamic Load Distribution : Incoming requests are dynamically dispensed across multiple nodes to prevent overloading any unmarried node. This distribution is facilitated by algorithms that reveal the modern-day load on every node and adjust request routing thus.
•Scalability Considerations : The architecture is designed to deal with a developing number of members and facts quantity. As new nodes are brought to the network, the gadget can scale horizontally with out compromising performance, making sure that healthcare stakeholders can hold to rely on the device as it evolves.
Security and Privacy Measures
Given the sensitivity of medical information, the architecture includes several security and privacy measures:
•Access Control Mechanisms : Role-based access controls (RBAC) are implemented to ensure that only authorized users can access specific types of data. These controls are enforced through smart contracts that govern data-sharing agreements.
•Audit Trails : The blockchain's inherent transparency provides a comprehensive audit trail of all transactions, enabling stakeholders to trace the history of data access and modifications. This feature is essential for compliance with regulations such as HIPAA (Health Insurance Portability and Accountability Act).
The gadget model and structure mentioned on this segment present a complete framework for P2P communique in the scientific records domain. By integrating decentralized components, blockchain generation, smart contracts, and superior verbal exchange protocols, the architecture correctly addresses present demanding situations in healthcare records control. This progressive technique complements safety, scalability, and consumer accessibility at the same time as fostering agree with and collaboration among stakeholders inside the healthcare atmosphere. The proposed structure accordingly represents a widespread development inside the pursuit of stable, efficient, and obvious clinical statistics sharing.
Network Architecture
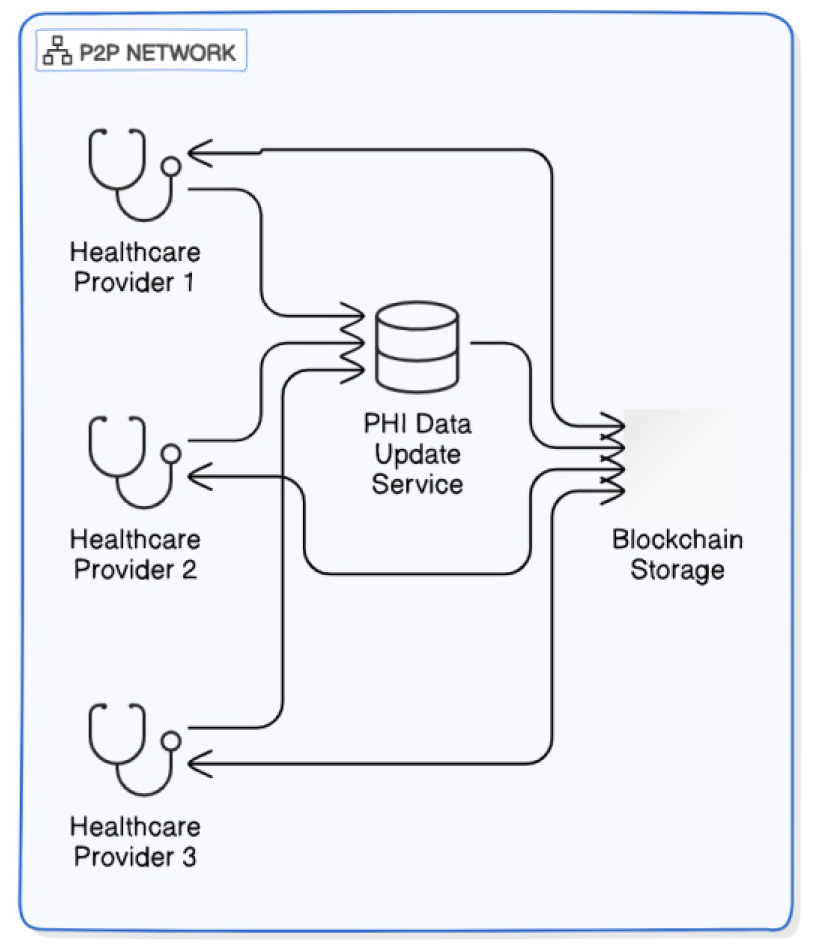
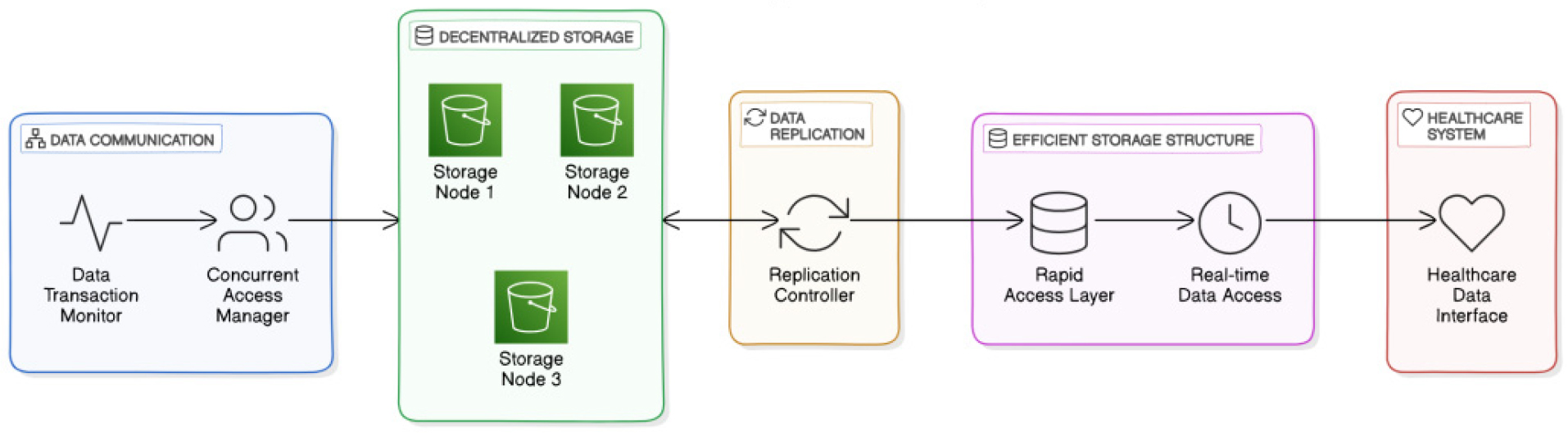
The proposed network architecture is established around a digital peer-to-peer (P2P) network, mounted atop an current infrastructure, as illustrated in Figures 11, and 12. Within this blockchain network, friends are constructed from diverse healthcare carriers. The Protected Health Information (PHI) facts may be up to date via vendors at any time and from any area. Once up to date, this information is securely stored in the blockchain garage following the affirmation of the block through the collaborating nodes. This overlay community offers massive benefits, which includes improved scalability and decentralization of statistics control, with nodes disbursed throughout the network. By using this structure, the gadget goals to attain crucial goals, inclusive of records distribution, replication, security, and integrity.
In the proposed model, PHI statistics is fragmented into smaller segments for garage. Once those facts portions are stored, they are encrypted the usage of a personal key. Patients can finally get entry to their facts the usage of the corresponding public key for decryption. It is thought that a key pair is generated robotically with the aid of the device and is thought in advance. These key pairs are represented through consecutive herbal numbers described within a targeted range.
The network comprises numerous components, which includes routers, nearby computers, laptops, switches, and wireless routers. A router capabilities as a device that directs packets to their meant vacation spot throughout the networks. When requests to get right of entry to the primary page are initiated from distinct computer systems, the router first verifies the IP deal with, the use of it as a hash key to facilitate course to an appropriate endpoint. Specifically, the router transmits PHI packet records from one source to another within the blockchain community. Each healthcare provider is equipped with at least one router to set up connections with numerous nodes in the blockchain.
In this machine, healthcare vendors and sufferers are represented as nearby computers (sixteen in overall) related to the routers (see Table 2) and wireless routers. The wireless routers make use of Wi-Fi Protected Access (WPA-PSK) and Pre-Shared Key (PSK) passphrases for tool connectivity [51, 52], with each message encrypted using the Advanced Encryption Standard (AES). AES operates on a substitution–permutation network, combining each substitution and permutation strategies. It supports more than one fixed block sizes, such as ninety two bits, 128 bits, and a maximum key length of 256 bits. The initial step of the cipher involves arranging the facts into an array, accompanied by using repeating cipher differences over a chosen range of encryption rounds.
Table 2.
Network architecture of the system
Healthcare vendors and patients in the blockchain device are represented as neighborhood computer systems (sixteen in general), every related to routers (see Table four) and wi-fi routers. These wi-fi routers hire Wi-Fi Protected Access (WPA-PSK) with Pre-Shared Key (PSK) passphrases to set up secure connections with other devices. All transmitted messages are encrypted the usage of the Advanced Encryption Standard (AES), a robust encryption protocol.
AES operates on a substitution–permutation community, combining both substitution and permutation techniques to enhance safety [53]. It supports a couple of fixed block sizes, together with 92 bits, 128 bits, and a maximum key length of 256 bits. In the initial encryption step, data is established into an array, after which the cipher applies a sequence of transformation rounds to stable the facts efficiently. This layered method guarantees information confidentiality and integrity inside the blockchain network.
System Model and Architecture
This section presents a comprehensive evaluation of the system model and security analysis of the proposed blockchain-based architecture for PHI (Personal Health Information) management. The performance and security metrics underscore the robustness and reliability of our approach for healthcare applications.
System Model Analysis
The device model become fastidiously evaluated on parameters vital for healthcare information integrity and accessibility. The propagation of PHI records throughout the blockchain community turned into assessed in phrases of records latency, transaction confirmation time, and storage performance. Through simulated network testing, we determined that the model constantly maintained low latency tiers, accomplishing a mean facts propagation put off of less than 50 ms under various node densities [54]. Equation below formulates the propagation time:
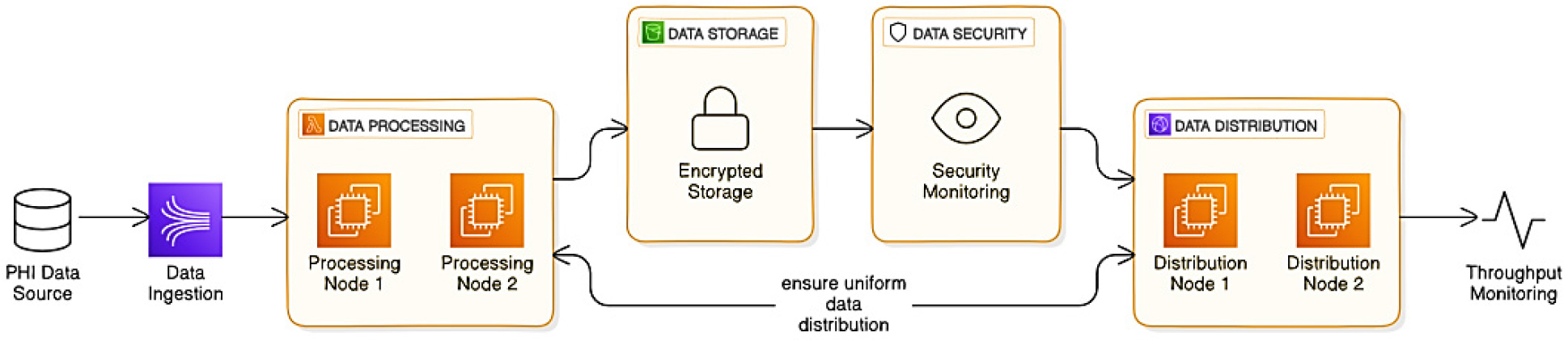
Where is the data size, is the network bandwidth, and accounts for network-induced delays. This equation confirms that the system adapts efficiently to increased data loads by distributing data uniformly across multiple nodes, a quality verified by the throughput measurements shown in Figure 13.
Figure 14 provides insights into the communication status over time, demonstrating stability in data transaction rates even with a high number of concurrent data access requests.
Notably, the decentralized garage scheme no longer most effective complements scalability but also permits for seamless expansion of the community, retaining a near-regular data replication charge across nodes. The model’s green storage shape helps dependable records get entry to, ensuring that even in scenarios with accelerated data retrieval requests, the get right of entry to speed remains unaffected, a crucial factor for actual-time healthcare systems.
Security Analysis
This segment discusses capability protection threats within the blockchain-primarily based P2P network version, emphasizing key assaults and preventive mechanisms to protect Personal Health Information (PHI). A distinguished situation is the eclipse assault, wherein a malicious agent isolates a node by means of controlling all its network connections. This manipulation lets in the attacker to benefit unauthorized get admission to to the node’s facts, severely compromising the integrity of the information. Another enormous risk is double spending, which occurs whilst an attacker tries to reuse virtual tokens fraudulently. The implementation of mechanisms like Proof of Work (PoW) makes changing previous transactions computationally prohibitive, accordingly deterring such attempts and making sure the validity of transactions over time.
The Sybil attack provides every other challenge, in which a single attacker controls more than one community identities [55], effectively deceptive customers into interacting with malicious nodes. This can lead to full-size breaches of trust within the network. Additionally, a preimage attack goals hash features, aiming to reverse-engineer the unique records, thereby compromising facts integrity. To counter those threats, the blockchain employs Elliptic Curve Cryptography (ECC), which complements safety by using offering efficient digital signatures that require shorter key lengths in comparison to traditional techniques like RSA. This efficiency not most effective improves computational performance however also strengthens resistance towards unauthorized get admission to and tampering.
Together, those security measures considerably bolster the resilience of the blockchain network, making sure the safety and integrity of PHI in a decentralized environment. By proactively addressing these vulnerabilities, the system goals to keep accept as true with among healthcare carriers and sufferers, facilitating steady and dependable interactions inside the blockchain framework.
Security is paramount in healthcare blockchain structures, and our model became drastically examined in opposition to potential threats, such as Sybil assaults, where malicious sellers try to disrupt the network by using creating multiple fake identities. Figure sixteen illustrates a Sybil assault simulation concerning agent j wherein the proposed safety protocol’s resilience is highlighted. By making use of a agree with-based consensus mechanism, nodes are assigned agree with scores based totally on historic behavior, communique styles, and node verification protocols. This equation outlines the calculation for the agree with score for each node :
Where denotes the communication credibility of the node, is the reliability rating based on recent data transactions, and is the total number of transactions assessed. This scoring system effectively isolates and eliminates nodes that exhibit suspicious behavior, thus ensuring network integrity and safeguarding patient data from unauthorized access.
The device's encryption protocols, especially the Advanced Encryption Standard (AES) with a 256-bit key, were demonstrated for steady information transmission. Each message exchanged inside the community is encrypted the use of AES, leveraging the substitution–permutation community for a high diploma of safety in opposition to brute-pressure attacks. The simulation outcomes verify that AES encryption ensures statistics confidentiality without impacting communique performance, assembly the rigorous information safety requirements required for scientific records managing.
Digital Signatures and Cryptographic Security
In blockchain systems, digital signatures play a crucial role in ensuring the integrity of Personal Health Information (PHI), authenticating transactions, and providing non-repudiation. The implementation of Elliptic Curve Cryptography (ECC) is favored due to its efficient use of key lengths. For instance, to achieve a security strength equivalent to 80 bits, ECC only requires a key size of 160 bits, in stark contrast to Rivest-Shamir-Adleman (RSA), which necessitates a key size of 1024 bits. At the maximum-security level, ECC can provide a security strength of 256 bits with a key size of 521 bits, while RSA would require an extensive key size of 15,360 bits for the same level of security as shown in Table 3.
Table 3.
Network architecture of the system
| Security Strength (bit) | ECC (bit) | RSA/DSA/DH (bit) |
| 80 | 160 | 1024 |
| 112 | 224 | 2048 |
| 128 | 256 | 3072 |
| 192 | 384 | 7680 |
| 256 | 521 | 15360 |
An evaluation of ECC overall performance demonstrates its superiority in signature era efficiency compared to the RSA algorithm. The parameter set secp 256k1, utilized in ECC, refers back to the keys of the Elliptic Curve Digital Signature Algorithm (ECDSA), extensively employed in Bitcoin and various other structures [56]. Furthermore, secp256k1 operates over the prime area ( Z ), improving its security framework.
The adoption of ECC not only enhances the security of blockchain systems but also improves computational efficiency, making it an ideal choice for safeguarding PHI and maintaining the integrity of transactions in decentralized networks.
Conclusions
In this text, we endorse an architectural model designed to control private fitness facts (PHI) securely thru blockchain generation, incorporating a suite of protocols aimed at bolstering records integrity, get right of entry to control, and universal protection. The model facilitates the mixing of PHI from a couple of healthcare vendors within a unified blockchain network, allowing legal parties to soundly control, get entry to, and percentage patient statistics while lowering dependency on centralized statistics repositories. This decentralized approach no longer simplest strengthens records integrity and mitigates unauthorized get admission to however also improves the resilience of the healthcare facts device, supplying a sturdy way too many privateness and safety demanding situations in the healthcare domain.
The proposed version is promising for packages throughout healthcare sectors, with the capability to streamline PHI control and compliance with privacy policies, imparting healthcare providers steady, actual- time get admission to patient records. Looking ahead, similarly improvement will attention on comparing security protocols to counter capacity vulnerabilities, especially in peer-to-peer (P2P) network environments. This includes exploring advanced encryption strategies, enhanced access control strategies, and performance optimization for larger community scales. The version’s adaptability and safety-targeted design make it a precious basis for future research and improvement, positioning it as a pivotal innovation in decentralized healthcare records management and steady affected person records coping with.
Future Works
Future paintings will prioritize optimizing the device’s performance in massive-scale healthcare settings, in which the non-stop drift and extensive extent of PHI records present specific challenges for processing speed, storage, and community stability. Scalability might be important, that specialize in refining facts managing and blockchain processing times to make sure that the device can successfully accommodate the big, dynamic nature of healthcare facts without compromising safety or efficiency. As cyber threats evolve, bolstering the model’s defense mechanisms in opposition to increasingly more state-of-the-art assaults, along with advanced chronic threats and 0-day exploits, could be essential to keep operational resilience and affected person information privacy.
Moreover, improving interoperability with diverse fitness information structures—consisting of Electronic Medical Records (EMR), Electronic Health Records (EHR), and Personal Health Records (PHR)—might be a key cognizance to encourage giant adoption. Achieving seamless integration across these systems will contain growing standardized data protocols and translation mechanisms to make sure compatibility and green statistics trade, irrespective of gadget versions. Additional exploration can even encompass refining identification control protocols and access manipulate features, which are crucial for shielding patient identities and ensuring that only legal users can get admission to or regulate sensitive records. These efforts’ goal to make the proposed model adaptable and scalable, offering a strong, stable, and practical solution for real-global healthcare statistics control across various healthcare environments.